To quickly spot unauthorized devices on your Wi-Fi router, check your router’s device list for unfamiliar names or IP addresses, change your Wi-Fi password regularly, and enable network encryption like WPA3. Using network scanning tools or the router’s admin interface can help identify unknown connections swiftly. Keeping a close eye on connected devices is key to maintaining your network’s security and preventing unauthorized access.
If you want to detect unauthorized devices on your Wi-Fi router, the first step is to log into your router’s admin panel and review the list of connected devices. Look for unfamiliar names or IP addresses that don’t belong to your household. You can also use third-party apps or network scanning tools like Fing or Wireless Network Watcher to get a detailed view of all connected devices. Regularly updating your password and enabling strong encryption further safeguards your network from intruders. Staying proactive in monitoring your Wi-Fi connections is essential for keeping your data safe and ensuring only trusted devices have access.
Having a secure Wi-Fi network is essential in today’s digital age, and one of the biggest concerns is unauthorized devices sneaking into your system. While it may seem daunting, detecting these intruders isn’t complicated once you know where to look and what tools to use. In this guide, we’ll walk you through simple yet effective ways to identify and block any device that shouldn’t be on your network, helping you safeguard your personal information and enjoy a secure browsing experience without worries.
How to Detect Unauthorized Devices on WiFi Router
Keeping your WiFi network secure is very important. Unauthorized devices can access your internet without permission, putting your personal information at risk. Learning how to spot these unwanted devices helps protect your privacy and prevent potential misuse of your network.
Understanding Why Unauthorized Devices Are a Problem
Unauthorized devices can use your WiFi connection to browse the internet, send spam, or even steal data. They might also slow down your internet speed because multiple devices are sharing the same bandwidth. Detecting these devices helps you regain control over who is connected to your network.
How Devices Connect to Your WiFi Network
Each device that connects to your WiFi network has a unique identifier called a MAC address. Routers also have an IP address assigned to each connected device. Knowing how devices connect makes it easier to identify unfamiliar or suspicious connections.
Step-by-Step Guide to Detect Unauthorized Devices
Check Your Router’s Admin Panel
The first way to see who is connected is by logging into your router’s admin panel. This panel displays a list of all devices currently connected to your WiFi. Usually, you can access it through a web browser by entering your router’s IP address.
Find Your Router’s IP Address
Most routers default to 192.168.1.1 or 192.168.0.1. You can find this information in your network settings. Once you enter this address into your browser, you’ll see the login screen for your router’s admin panel.
Log Into Your Router
Use your admin username and password to access the router settings. If you haven’t changed these details, they are usually printed on the router or provided in the manual. For security, consider changing default credentials.
Locate the List of Connected Devices
Inside the admin panel, look for sections labeled “Connected Devices,” “Attached Devices,” or “Device List.” This section shows the devices currently connected to your network, including their IP and MAC addresses.
Review the Device List Carefully
Check each device for familiarity. Recognize devices belonging to your family members or your own gadgets. If you see unfamiliar devices, it’s a sign someone else might be connected.
Using Network Monitoring Tools
For advanced users or those wanting more details, network monitoring tools provide comprehensive insights. These tools scan your network and identify all connected devices, even in the background.
Popular Network Monitoring Options
- Fing: An easy-to-use app available for smartphones and desktops that detects all devices on your network.
- GlassWire: A network security tool that shows real-time device activity and alerts you to new connections.
- Wireshark: Advanced network analysis software suitable for experienced users who want detailed traffic data.
Detecting Suspicious Devices Based on Device Details
Once you have a list of devices, analyze their details. Look for names or MAC addresses that look unfamiliar or suspicious. Some devices might have generic names like “Android,” “Unknown,” or random characters.
Understanding MAC Addresses
MAC addresses are unique identifiers assigned to network interfaces. They are usually formatted as six pairs of hexadecimal digits, like 00:1A:2B:3C:4D:5E. If you see a MAC address that doesn’t match your known devices, it warrants further investigation.
How to Identify Unknown Devices
- Compare MAC addresses with your known devices’ MAC addresses.
- Check if the IP addresses match devices you recognize.
- Consider the device’s connection time and data usage — unfamiliar devices with high data use may be suspicious.
Securing Your WiFi to Prevent Unauthorized Access
Preventing unauthorized devices from connecting is the best way to maintain a secure network. Changing your WiFi password regularly is an effective safeguard.
Strengthening Password Security
- Use a complex password that combines letters, numbers, and symbols.
- Avoid common words or predictable patterns.
- Update your password at least every few months.
Enabling Network Encryption
Choose the highest encryption method your router supports, typically WPA3 or WPA2. This encrypts the data transmitted over your network, making it difficult for outsiders to access your information.
Disabling WPS
Wi-Fi Protected Setup (WPS) can be a security weak point. Disabling WPS on your router enhances security and reduces the chance of unauthorized device connections.
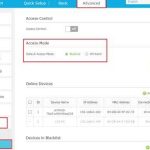
Using MAC Address Filtering
This feature allows your router to accept only devices with specific MAC addresses. While not foolproof, MAC filtering adds an extra layer of control over device access.
How to Set Up MAC Filtering
- Access your router’s admin panel.
- Navigate to the MAC filtering or device access section.
- Add the MAC addresses of your trusted devices.
- Enable the filtering mode to block unknown devices.
Detecting unauthorized devices on your WiFi router involves regularly checking your device list, understanding device details, and implementing security measures. Maintaining control over your network helps protect your personal information and keeps your internet running smoothly. By following these steps, you can quickly identify and block unwanted connections, ensuring your WiFi remains safe and secure for everyone in your home.
How To See Who's Connected To Your WiFi Router
Frequently Asked Questions
How can I access the list of devices connected to my Wi-Fi router?
Log into your router’s admin panel through a web browser using the router’s IP address, typically 192.168.1.1 or 192.168.0.1. Enter your username and password, then navigate to the section labeled “Connected Devices,” “Device List,” or similar. This page displays all devices currently connected to your network, including their IP addresses, MAC addresses, and device names, helping you identify any unfamiliar connections.
What signs indicate there may be unauthorized devices on my network?
If you notice unknown devices listed in your router’s connected devices, especially those with unfamiliar names or MAC addresses, it could point to unauthorized access. Other signs include unexpected drops in network speed, increased network activity, or if your devices experience unusual behavior. Regularly monitoring your connected devices helps you spot potential intrusions early.
What steps should I take if I find an unauthorized device?
Immediately change your Wi-Fi password to block the unauthorized device from reconnecting. Consider updating your router’s firmware to ensure security patches are installed. You can also enable network security features such as MAC address filtering to restrict access to known devices. If necessary, perform a factory reset on your router and reconfigure the security settings to prevent future unauthorized access.
Can I set up alerts for new devices connecting to my Wi-Fi?
Many modern routers include features that notify you when new devices connect. Access your router’s settings and look for options like “Device Alerts,” “Notification Settings,” or similar. Enable these alerts to receive email or app notifications when a new device connects. This proactive approach helps you monitor your network for unauthorized access in real-time.
Are there third-party tools to help detect unauthorized devices?
Yes, several network scanning and monitoring tools can help identify devices on your network. Applications like Fing, Advanced IP Scanner, or Wireshark allow you to scan your network and see all connected devices. Regularly using these tools enhances your ability to detect unfamiliar devices and maintain network security effectively.
Final Thoughts
To detect unauthorized devices on a wifi router, regularly check the device list in your router’s settings. Use your router’s admin interface to identify unfamiliar MAC addresses or IP addresses. Set up alerts for new device connections if your router offers this feature.
By maintaining vigilance, you ensure your network remains secure. Remember, how to detect unauthorized devices on wifi router is essential to prevent unauthorized access and protect your data. Staying proactive keeps your network safe and your devices secure.